Client
A fast-growing SaaS platform offering multi-user access across web and mobile apps. As their user base grew, their old login system couldn’t handle the load and lacked security controls.
They needed:
-
Secure login
-
Scalable token management
-
Role-based access control
-
Support for multiple user types
-
OAuth2 compatibility
-
Zero downtime authentication flow
Project Overview
We built a modern, scalable, cloud-ready authentication and authorization system that supports:
-
JWT-based stateless authentication
-
OAuth2 provider integration
-
Session-based fallback (optional)
-
RBAC (Role-Based Access Control)
-
Secure refresh token lifecycle
-
User/device-level access rules
Designed to handle millions of tokens and thousands of concurrent logins.
Key Challenges
1. Legacy Auth System
The old system used simple sessions with no refresh tokens and limited security.
2. Multi-Tenant Requirements
Different departments and user types required different access levels.
3. Scalability
Auth system had to handle:
-
Peak login spikes
-
Mobile apps refreshing tokens
-
API gateways validating millions of requests
4. Security
Protection needed against:
-
Token theft
-
Session hijacking
-
CSRF
-
Bruteforce attacks
-
Improper authorization checks
Our Solution
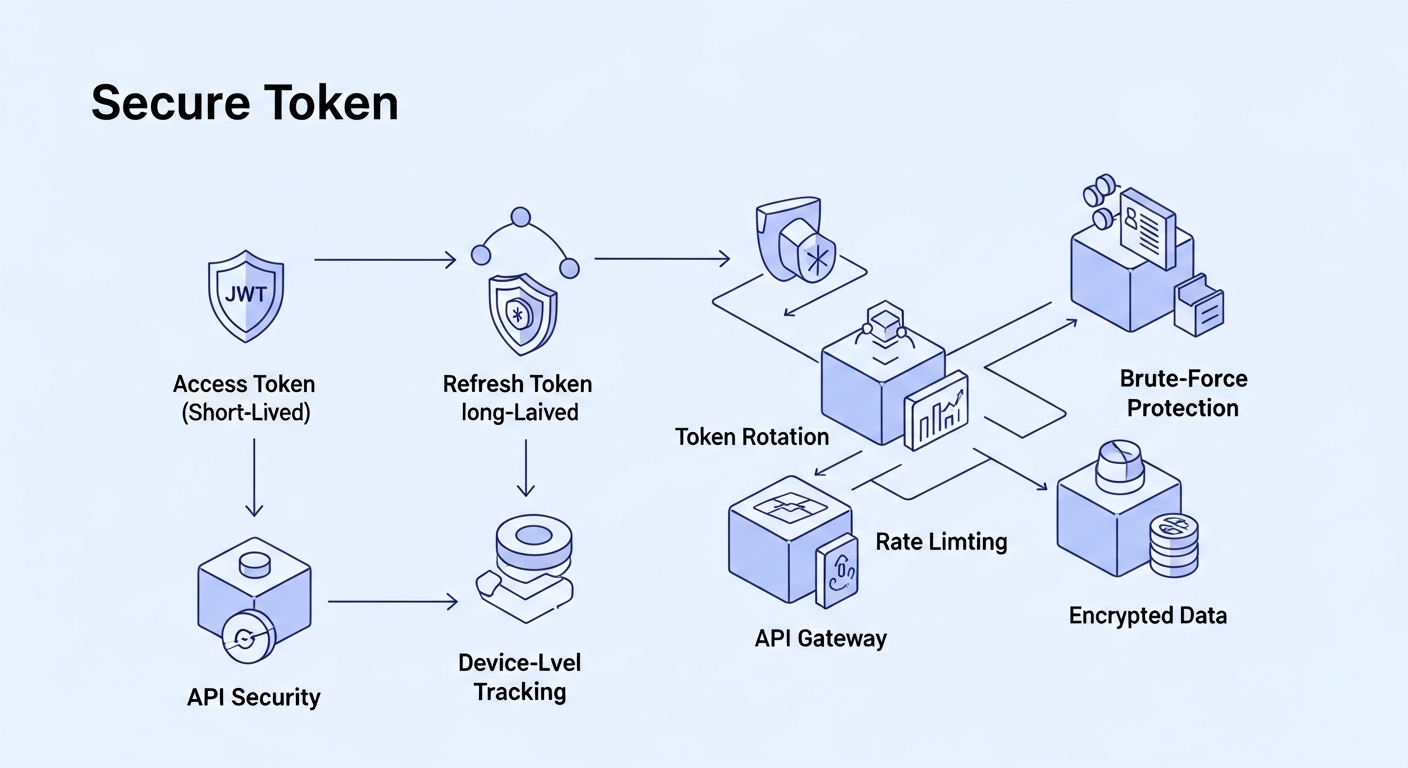
1. Implementing JWT-Based Authentication
JWT was chosen for:
-
Stateless validation
-
No server-side session storage
-
Fast API gateway validation
We used:
-
Access Tokens (short-lived)
-
Refresh Tokens (long-lived) stored securely
-
Rotating tokens to prevent replay attacks
-
Device-wise token tracking
Security Features:
-
HS256/RS256 signing
-
Token blacklist for compromised tokens
-
Strict expiry and refresh logic
2. OAuth2 Integration for Third-Party Access
We enabled OAuth2 flows:
-
Authorization Code Flow (web)
-
PKCE (mobile)
-
Client Credentials Flow (server-to-server)
Supported providers:
-
Google
-
Microsoft
-
GitHub
-
Enterprise SSO (via OpenID Connect)
This enabled:
-
Quick onboarding
-
Single sign-on (SSO)
-
Secure federated login
3. Optional Session-Based Authentication
For internal admin apps, we provided session-based auth:
-
Secure cookies
-
SameSite + HTTPOnly flags
-
Server-side session store (Redis for performance)
4. Role-Based Access Control (RBAC)
We implemented a flexible RBAC system:
Entities:
-
Roles (Admin, Manager, Staff, Customer, API Client)
-
Permissions (read, write, delete, approve, upload)
-
Resources/Modules
Dynamic:
-
Roles can be assigned dynamically
-
Permissions checked at request-time
-
Fine-grained access rules
All validation happens via:
-
Middleware interceptors
-
API gateway policies
-
Attribute-based checks (optional)
5. Central Authentication Server (Auth Service)
We built a dedicated microservice for authentication:
-
Sign-in / Sign-up
-
Refresh tokens
-
Password reset
-
OAuth2 callback handling
-
JWT issuance/validation
This ensured clean separation and easy scaling.
6. Hardening & Security Controls
Included:
-
Password hashing (Argon2 / bcrypt)
-
Rate limiting for login endpoints
-
MFA/Two-Factor Authentication (optional)
-
IP/device-based restrictions
-
Audit logs of auth events
-
Email + mobile verification
-
Brute-force detection
7. API Gateway Integration
To secure downstream microservices:
-
Token validation at gateway
-
RBAC validation at gateway or service layer
-
Central logging & observability
This reduced load on backend microservices.
Architecture Diagram (Text Version)
Results & Impact
🟢 Zero Downtime Auth
New system deployed without breaking sessions or tokens.
🔒 Strong Security
256-bit JWT signing, MFA, RBAC — all in place.
💨 Fast Token Validation
Stateless JWT validation improved request latency significantly.
📈 Scalable Authentication
Handles:
-
Millions of tokens
-
1000s of concurrent logins
-
Mobile + Web traffic
👥 Secure Multi-User Environment
Fine-grained RBAC ensures every user sees only what they’re allowed to.
🔁 Reduced Auth-Related Errors
Clear flows + better token lifecycle = fewer support tickets.
Conclusion
By designing a scalable authentication and authorization system with JWT, OAuth2, and RBAC, we gave the client a future-proof security foundation.
The system is now:
-
Robust
-
Scalable
-
Secure
-
Easy to extend
-
Suitable for multi-tenant platforms
A strong backbone for user identity, access control, and API protection.

Written by
Oliver Thomas
Oliver Thomas is a passionate developer and tech writer. He crafts innovative solutions and shares insightful tech content with clarity and enthusiasm.